id
stringlengths 12
47
| title
stringlengths 0
256
⌀ | description
stringlengths 3
139k
| cpes
sequencelengths 0
5.42k
| cvss_v4_0
float64 0
10
⌀ | cvss_v3_1
float64 0
10
⌀ | cvss_v3_0
float64 0
10
⌀ | cvss_v2_0
float64 0
10
⌀ |
|---|---|---|---|---|---|---|---|
GHSA-wfgf-2q6h-cjmv | PHP remote file inclusion vulnerability in external.php in PHPCityPortal allows remote attackers to execute arbitrary PHP code via a URL in the url parameter. | [] | null | null | null | null |
|
GHSA-5cq8-4jvq-q85v | Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') vulnerability in NotFound Sticky Button allows Stored XSS. This issue affects Sticky Button: from n/a through 1.0. | [] | null | 7.1 | null | null |
|
CVE-2023-2344 | SourceCodester Service Provider Management System HTTP POST Request sql injection | A vulnerability has been found in SourceCodester Service Provider Management System 1.0 and classified as critical. Affected by this vulnerability is an unknown functionality of the file /classes/Master.php?f=save_service of the component HTTP POST Request Handler. The manipulation of the argument name leads to sql injection. The attack can be launched remotely. The exploit has been disclosed to the public and may be used. The associated identifier of this vulnerability is VDB-227587. | [
"cpe:2.3:a:oretnom23:service_provider_management_system:1.0:*:*:*:*:*:*:*"
] | null | 6.3 | 6.3 | 6.5 |
GHSA-v938-m8gq-54wh | Improper Neutralization of Argument Delimiters in a Command ('Argument Injection') vulnerability in TCP function included in the firmware of Mitsubishi Electric MELQIC IU1 series IU1-1M20-D firmware version 1.0.7 and earlier allows an attacker on the same network segment to stop the network functions or execute malware via a specially crafted packet. | [] | null | null | null | null |
|
GHSA-cwv3-863g-39vx | Stack overflow due to looping TFLite subgraph | ImpactTFlite graphs must not have loops between nodes. However, this condition was not checked and an attacker could craft models that would result in infinite loop during evaluation. In certain cases, the infinite loop would be replaced by stack overflow due to too many recursive calls.For example, the [`While` implementation](https://github.com/tensorflow/tensorflow/blob/106d8f4fb89335a2c52d7c895b7a7485465ca8d9/tensorflow/lite/kernels/while.cc) could be tricked into a scneario where both the body and the loop subgraphs are the same. Evaluating one of the subgraphs means calling the `Eval` function for the other and this quickly exhaust all stack space.PatchesWe have patched the issue in GitHub commit [9c1dc920d8ffb4893d6c9d27d1f039607b326743](https://github.com/tensorflow/tensorflow/commit/9c1dc920d8ffb4893d6c9d27d1f039607b326743) (for the `While` operator) and in GitHub commit [c6173f5fe66cdbab74f4f869311fe6aae2ba35f4](https://github.com/tensorflow/tensorflow/commit/c6173f5fe66cdbab74f4f869311fe6aae2ba35f4) (in general).The fix will be included in TensorFlow 2.5.0. We will also cherrypick this commit on TensorFlow 2.4.2, TensorFlow 2.3.3, TensorFlow 2.2.3 and TensorFlow 2.1.4, as these are also affected and still in supported range.For more informationPlease consult [our security guide](https://github.com/tensorflow/tensorflow/blob/master/SECURITY.md) for more information regarding the security model and how to contact us with issues and questions.AttributionThis vulnerability has been reported by members of the Aivul Team from Qihoo 360. | [] | 7 | 7.3 | null | null |
RHSA-2020:1372 | Red Hat Security Advisory: kernel security and bug fix update | kernel: powerpc: local user can read vector registers of other users' processes via a Facility Unavailable exception kernel: powerpc: local user can read vector registers of other users' processes via an interrupt kernel: powerpc: incomplete Spectre-RSB mitigation leads to information exposure kernel: use-after-free caused by a malicious USB device in the drivers/hid/usbhid/hiddev.c driver | [
"cpe:/a:redhat:enterprise_linux:8::crb",
"cpe:/o:redhat:enterprise_linux:8::baseos"
] | null | 6.8 | null | null |
CVE-2014-2641 | Cross-site request forgery (CSRF) vulnerability in HP System Management Homepage (SMH) before 7.4 allows remote authenticated users to hijack the authentication of unspecified victims via unknown vectors. | [
"cpe:2.3:a:hp:system_management_homepage:*:*:*:*:*:*:*:*",
"cpe:2.3:a:hp:system_management_homepage:7.0:*:*:*:*:*:*:*",
"cpe:2.3:a:hp:system_management_homepage:7.1:*:*:*:*:*:*:*",
"cpe:2.3:a:hp:system_management_homepage:7.2:*:*:*:*:*:*:*",
"cpe:2.3:a:hp:system_management_homepage:7.2.1:*:*:*:*:*:*:*"
] | null | null | null | 6 |
|
CVE-2024-53067 | scsi: ufs: core: Start the RTC update work later | In the Linux kernel, the following vulnerability has been resolved:
scsi: ufs: core: Start the RTC update work later
The RTC update work involves runtime resuming the UFS controller. Hence,
only start the RTC update work after runtime power management in the UFS
driver has been fully initialized. This patch fixes the following kernel
crash:
Internal error: Oops: 0000000096000006 [#1] PREEMPT SMP
Workqueue: events ufshcd_rtc_work
Call trace:
_raw_spin_lock_irqsave+0x34/0x8c (P)
pm_runtime_get_if_active+0x24/0x9c (L)
pm_runtime_get_if_active+0x24/0x9c
ufshcd_rtc_work+0x138/0x1b4
process_one_work+0x148/0x288
worker_thread+0x2cc/0x3d4
kthread+0x110/0x114
ret_from_fork+0x10/0x20 | [
"cpe:2.3:o:linux:linux_kernel:*:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.12:rc1:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.12:rc2:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.12:rc3:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.12:rc4:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.12:rc5:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.12:rc6:*:*:*:*:*:*"
] | null | 5.5 | null | null |
CVE-2006-4336 | Buffer underflow in the build_tree function in unpack.c in gzip 1.3.5 allows context-dependent attackers to execute arbitrary code via a crafted leaf count table that causes a write to a negative index. | [
"cpe:2.3:a:gzip:gzip:1.3.5:*:*:*:*:*:*:*"
] | null | null | null | 7.5 |
|
CVE-2024-30451 | WordPress Geo Controller plugin <= 8.6.4 - Cross Site Scripting (XSS) vulnerability | Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') vulnerability in INFINITUM FORM Geo Controller allows Stored XSS.This issue affects Geo Controller: from n/a through 8.6.4.
| [] | null | 6.5 | null | null |
GHSA-8mg5-cwcv-658x | FileRun (version 2017.09.18 and below) suffers from a remote SQL injection vulnerability due to a failure to sanitize input in the metafield parameter inside the metasearch module (under the search function). | [] | null | null | 9.8 | null |
|
GHSA-7p95-34jm-7r5r | In hevc codec, there is an out-of-bounds write due to an incorrect bounds check with the i2_pic_width_in_luma_samples value. This could lead to remote escalation of privilege with no additional execution privileges needed. User interaction is needed for exploitation. Product: Android. Versions: 7.0, 7.1.1, 7.1.2, 8.0, 8.1. Android ID: A-65483665. | [] | null | null | 8.8 | null |
|
CVE-2023-49277 | Reflected Cross-site Scripting Vulnerability in dpaste | dpaste is an open source pastebin application written in Python using the Django framework. A security vulnerability has been identified in the expires parameter of the dpaste API, allowing for a POST Reflected XSS attack. This vulnerability can be exploited by an attacker to execute arbitrary JavaScript code in the context of a user's browser, potentially leading to unauthorized access, data theft, or other malicious activities. Users are strongly advised to upgrade to dpaste release v3.8 or later versions, as dpaste versions older than v3.8 are susceptible to the identified security vulnerability. No known workarounds have been identified, and applying the patch is the most effective way to remediate the vulnerability. | [
"cpe:2.3:a:darrennathanael:dpaste:*:*:*:*:*:*:*:*"
] | null | 8.3 | null | null |
GHSA-87v6-vw3p-5g5r | LINK-NET LW-N605R devices with firmware 12.20.2.1486 allow Remote Code Execution via shell metacharacters in the HOST field of the ping feature at adm/systools.asp. Authentication is needed but the default password of admin for the admin account may be used in some cases. | [] | null | null | 8.8 | null |
|
RHSA-2016:0590 | Red Hat Security Advisory: spacewalk-java security update | Satellite: stored XSS in user details fields (incomplete fix for CVE-2014-7811) 5: multiple stored XSS vulnerabilities 5: stored and reflected XSS vulnerabilities spacewalk-java: Multiple XSS issues in WebUI | [
"cpe:/a:redhat:network_satellite:5.7::el6"
] | null | null | null | null |
CVE-2020-14492 | OpenClinic GA | OpenClinic GA 5.09.02 and 5.89.05b does not properly neutralize user-controllable input, which may allow the execution of malicious code within the user’s browser. | [
"cpe:2.3:a:openclinic_ga_project:openclinic_ga:5.09.02:*:*:*:*:*:*:*",
"cpe:2.3:a:openclinic_ga_project:openclinic_ga:5.89.05b:*:*:*:*:*:*:*"
] | null | 5.4 | null | null |
GHSA-vhvh-8f85-cw7p | The odbc_bindcols function in ext/odbc/php_odbc.c in PHP before 5.6.12 mishandles driver behavior for SQL_WVARCHAR columns, which allows remote attackers to cause a denial of service (application crash) in opportunistic circumstances by leveraging use of the odbc_fetch_array function to access a certain type of Microsoft SQL Server table. | [] | null | null | 7.5 | null |
|
CVE-2019-10449 | Jenkins Fortify on Demand Plugin stores credentials unencrypted in job config.xml files on the Jenkins master where they can be viewed by users with Extended Read permission, or access to the master file system. | [
"cpe:2.3:a:jenkins:fortify_on_demand:*:*:*:*:*:jenkins:*:*"
] | null | 8.8 | null | 4 |
|
CVE-2013-0392 | Unspecified vulnerability in the PeopleSoft PeopleTools component in Oracle PeopleSoft Products 8.51 and 8.52 allows remote attackers to affect integrity via unknown vectors related to Portal, a different vulnerability than CVE-2012-5059. | [
"cpe:2.3:a:oracle:peoplesoft_products:8.51:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:peoplesoft_products:8.52:*:*:*:*:*:*:*"
] | null | null | null | 4.3 |
|
GHSA-6qf5-8x9x-hm85 | The Mosaic theme for WordPress is vulnerable to Stored Cross-Site Scripting via the ‘link’ parameter within the theme's Button shortcode in all versions up to, and including, 1.7.1 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | [] | null | 6.4 | null | null |
|
CVE-2009-3010 | Mozilla Firefox 3.0.13 and earlier, 3.5, 3.6 a1 pre, and 3.7 a1 pre; SeaMonkey 1.1.17; and Mozilla 1.7.x and earlier do not properly block data: URIs in Refresh headers in HTTP responses, which allows remote attackers to conduct cross-site scripting (XSS) attacks via vectors related to (1) injecting a Refresh header that contains JavaScript sequences in a data:text/html URI or (2) entering a data:text/html URI with JavaScript sequences when specifying the content of a Refresh header. NOTE: in some product versions, the JavaScript executes outside of the context of the HTTP site. | [
"cpe:2.3:a:mozilla:firefox:*:*:*:*:*:*:*:*",
"cpe:2.3:a:mozilla:firefox:3.5:*:*:*:*:*:*:*",
"cpe:2.3:a:mozilla:firefox:3.6:a1_prerelease:*:*:*:*:*:*",
"cpe:2.3:a:mozilla:firefox:3.7:a1_prerelease:*:*:*:*:*:*",
"cpe:2.3:a:mozilla:mozilla:*:*:*:*:*:*:*:*",
"cpe:2.3:a:mozilla:seamonkey:1.1.17:*:*:*:*:*:*:*"
] | null | null | null | 4.3 |
|
CVE-2022-28543 | Path traversal vulnerability in Samsung Flow prior to version 4.8.07.4 allows local attackers to read arbitrary files as Samsung Flow permission. | [
"cpe:2.3:a:samsung:samsung_flow:*:*:*:*:*:*:*:*"
] | null | 4 | null | null |
|
CVE-2022-31108 | Arbitrary `CSS` injection into the generated graph affecting the container HTML in mermaid.js | Mermaid is a JavaScript based diagramming and charting tool that uses Markdown-inspired text definitions and a renderer to create and modify complex diagrams. An attacker is able to inject arbitrary `CSS` into the generated graph allowing them to change the styling of elements outside of the generated graph, and potentially exfiltrate sensitive information by using specially crafted `CSS` selectors. The following example shows how an attacker can exfiltrate the contents of an input field by bruteforcing the `value` attribute one character at a time. Whenever there is an actual match, an `http` request will be made by the browser in order to "load" a background image that will let an attacker know what's the value of the character. This issue may lead to `Information Disclosure` via CSS selectors and functions able to generate HTTP requests. This also allows an attacker to change the document in ways which may lead a user to perform unintended actions, such as clicking on a link, etc. This issue has been resolved in version 9.1.3. Users are advised to upgrade. Users unable to upgrade should ensure that user input is adequately escaped before embedding it in CSS blocks. | [
"cpe:2.3:a:mermaid_project:mermaid:*:*:*:*:*:node.js:*:*"
] | null | 4.1 | null | null |
GHSA-369r-wm99-xh2c | Reflected Cross-Site Scripting (XSS) vulnerability in version 1.0 of the Clinic Queuing System. This vulnerability could allow an attacker to execute JavaScript code in the victim's browser by sending a malicious URL through the page parameter in /patient_side.php. | [] | 4.8 | null | null | null |
|
GHSA-vhph-j65g-6fqq | setcookie.php for the administration login in Professional Home Page Tools Guestbook records the hash of the administrator password in a cookie, which allows attackers to conduct brute force password guessing attacks after obtaining the hash. | [] | null | null | null | null |
|
GHSA-x3w4-7cmr-9gv2 | If an attacker can get a user to open a specially prepared directory tree as a workspace in Visual Studio Code with the CodeQL extension active, arbitrary code of the attacker's choosing may be executed on the user's behalf. This is fixed in version 1.0.1 of the extension. Users should upgrade to this version using Visual Studio Code Marketplace's upgrade mechanism. After upgrading, the codeQL.cli.executablePath setting can only be set in the per-user settings, and not in the per-workspace settings. More information about VS Code settings can be found here. | [] | null | null | null | null |
|
GHSA-5vqx-jv2p-m95q | The xenDaemonListDefinedDomains function in xen/xend_internal.c in libvirt 1.1.1 allows remote authenticated users to cause a denial of service (memory corruption and crash) via vectors involving the virConnectListDefinedDomains API function. | [] | null | null | null | null |
|
CVE-2021-44696 | Adobe Prelude JPEG File Parsing Out-Of-Bounds Read Information Disclosure Vulnerability | Adobe Prelude version 22.1.1 (and earlier) is affected by an out-of-bounds read vulnerability that could lead to disclosure of sensitive memory. An attacker could leverage this vulnerability to bypass mitigations such as ASLR. Exploitation of this issue requires user interaction in that a victim must open a malicious JPEG file. | [
"cpe:2.3:a:adobe:prelude:*:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:macos:-:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows:-:*:*:*:*:*:*:*"
] | null | 3.3 | null | null |
CVE-2016-3247 | Microsoft Internet Explorer 11 and Microsoft Edge allow remote attackers to execute arbitrary code or cause a denial of service (memory corruption) via a crafted web site, aka "Microsoft Browser Memory Corruption Vulnerability." | [
"cpe:2.3:a:microsoft:edge:-:*:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:internet_explorer:11:-:*:*:*:*:*:*"
] | null | null | 7.5 | 5.1 |
|
CVE-2000-0424 | The CGI counter 4.0.7 by George Burgyan allows remote attackers to execute arbitrary commands via shell metacharacters. | [
"cpe:2.3:a:george_burgyan:cgi_counter:4.0.2:*:*:*:*:*:*:*",
"cpe:2.3:a:george_burgyan:cgi_counter:4.0.7:*:*:*:*:*:*:*"
] | null | null | null | 7.5 |
|
GHSA-wv24-h4q9-q4cm | The GD Rating System plugin 2.3 for WordPress has Directory Traversal in the wp-admin/admin.php panel parameter for the gd-rating-system-transfer page. | [] | null | null | 7.5 | null |
|
CVE-2019-19220 | BMC Control-M/Agent 7.0.00.000 allows OS Command Injection (issue 2 of 2). | [
"cpe:2.3:a:bmcsoftware:control-m\\/agent:7.0.00.000:*:*:*:*:*:*:*"
] | null | 8.8 | null | 8.5 |
|
CVE-2022-41528 | TOTOLINK NR1800X V9.1.0u.6279_B20210910 was discovered to contain an authenticated stack overflow via the text parameter in the setSmsCfg function. | [
"cpe:2.3:o:totolink:nr1800x_firmware:9.1.0u.6279_b20210910:*:*:*:*:*:*:*",
"cpe:2.3:h:totolink:nr1800x:-:*:*:*:*:*:*:*"
] | null | 8.8 | null | null |
|
GHSA-pg7r-qqvh-q4vw | Heap-based buffer overflow in Shim allows remote attackers to execute arbitrary code via a crafted IPv6 address, related to the "tftp:// DHCPv6 boot option." | [] | null | null | null | null |
|
RHSA-2024:10665 | Red Hat Security Advisory: ACS 4.4 enhancement and security update | cross-spawn: regular expression denial of service | [
"cpe:/a:redhat:advanced_cluster_security:4.4::el8"
] | null | 4.4 | null | null |
GHSA-gmw5-xjxq-3255 | A stored Cross Site Scripting vulnerability in the "related recommendations" feature in Ppress v.0.0.9 allows a remote attacker to execute arbitrary code via a crafted script to the article.title, article.category, and article.tags parameters. | [] | null | 6.5 | null | null |
|
GHSA-mmh6-5cpf-2c72 | phpMyFAQ Path Traversal in Attachments | SummaryThere is a Path Traversal vulnerability in Attachments that allows attackers with admin rights to upload malicious files to other locations of the web root.PoCIn settings, the attachment location is vulnerable to path traversal and can be set to e.g ..\hacked
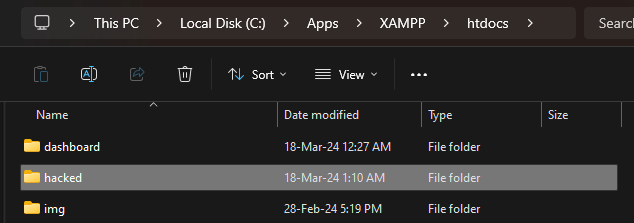
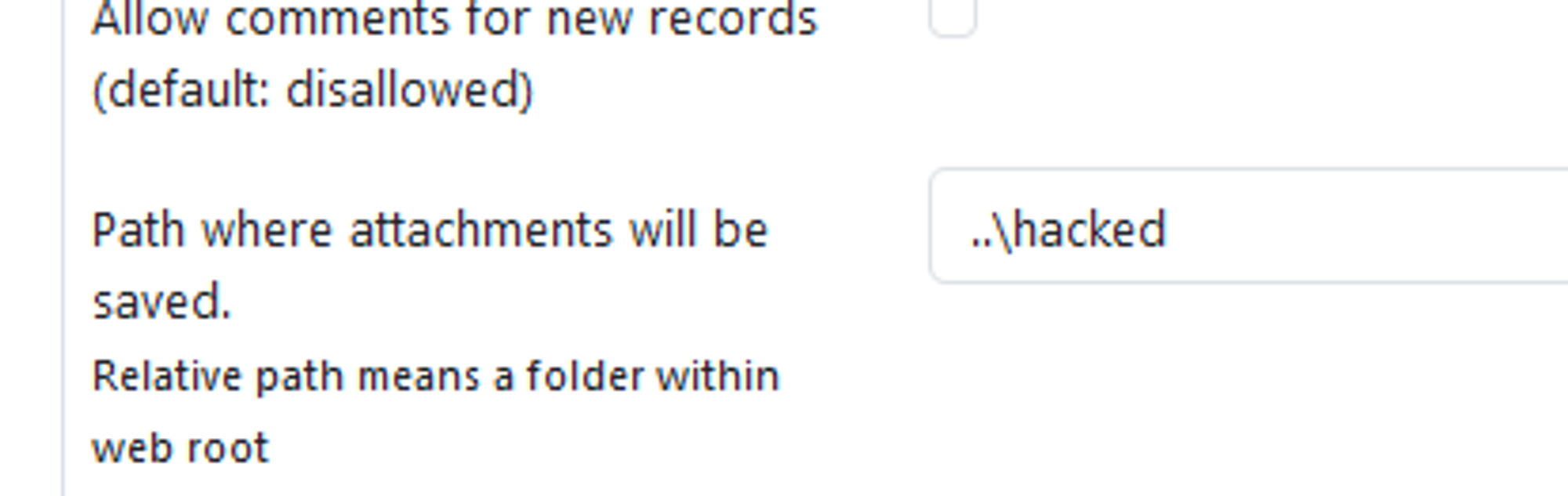When the above is set, attachments files are now uploaded to e.g C:\Apps\XAMPP\htdocs\hacked instead of C:\Apps\XAMPP\htdocs\phpmyfaq\attachmentsVerify this by uploading an attachment and see that the "hacked" directory is now created in the web root folder with the attachment file inside.
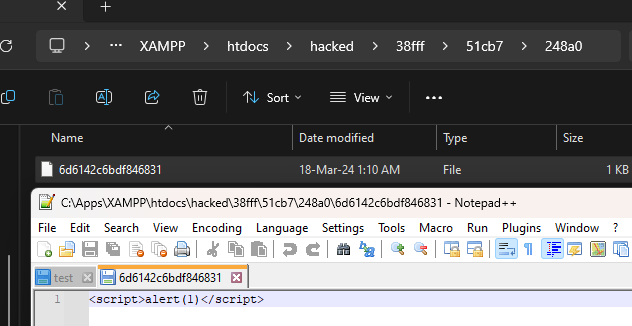ImpactAttackers can potentially upload malicious files outside the specified directory. | [] | null | 3.8 | null | null |
CVE-2021-25483 | Lack of boundary checking of a buffer in livfivextractor library prior to SMR Oct-2021 Release 1 allows OOB read. | [
"cpe:2.3:o:google:android:8.1:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:9.0:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:10.0:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:11.0:*:*:*:*:*:*:*"
] | null | 4 | null | null |
|
CVE-2019-8212 | Adobe Acrobat and Reader versions , 2019.012.20040 and earlier, 2017.011.30148 and earlier, 2017.011.30148 and earlier, 2015.006.30503 and earlier, and 2015.006.30503 and earlier have an use after free vulnerability. Successful exploitation could lead to arbitrary code execution . | [
"cpe:2.3:a:adobe:acrobat_dc:*:*:*:*:classic:*:*:*",
"cpe:2.3:a:adobe:acrobat_dc:*:*:*:*:continuous:*:*:*",
"cpe:2.3:a:adobe:acrobat_reader_dc:*:*:*:*:classic:*:*:*",
"cpe:2.3:a:adobe:acrobat_reader_dc:*:*:*:*:continuous:*:*:*",
"cpe:2.3:o:apple:macos:-:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows:-:*:*:*:*:*:*:*"
] | null | 9.8 | null | 7.5 |
|
RHSA-2021:0848 | Red Hat Security Advisory: kernel security update | kernel: performance counters race condition use-after-free | [
"cpe:/o:redhat:rhel_aus:7.3::server"
] | null | 7 | null | null |
CVE-2021-40059 | There is a permission control vulnerability in the Wi-Fi module. Successful exploitation of this vulnerability may affect confidentiality. | [
"cpe:2.3:o:huawei:emui:10.1.0:*:*:*:*:*:*:*",
"cpe:2.3:o:huawei:emui:10.1.1:*:*:*:*:*:*:*",
"cpe:2.3:o:huawei:emui:11.0.0:*:*:*:*:*:*:*",
"cpe:2.3:o:huawei:emui:11.0.1:*:*:*:*:*:*:*",
"cpe:2.3:o:huawei:emui:12.0.0:*:*:*:*:*:*:*",
"cpe:2.3:o:huawei:magic_ui:3.1.0:*:*:*:*:*:*:*",
"cpe:2.3:o:huawei:magic_ui:3.1.1:*:*:*:*:*:*:*",
"cpe:2.3:o:huawei:magic_ui:4.0.0:*:*:*:*:*:*:*"
] | null | 6.5 | null | 3.3 |
|
GHSA-6fxx-g64m-phpw | In WiFi tethering, there is a possible attacker controlled intent due to an unsafe PendingIntent. This could lead to local escalation of privilege with User execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-11Android ID: A-156353008 | [] | null | null | null | null |
|
GHSA-jp58-xphf-m4g6 | Multiple SQL injection vulnerabilities in the Wysija Newsletters plugin before 2.2.1 for WordPress allow remote authenticated administrators to execute arbitrary SQL commands via the (1) search or (2) orderby parameter to wp-admin/admin.php. NOTE: this can be leveraged using CSRF to allow remote unauthenticated attackers to execute arbitrary SQL commands. | [] | null | null | null | null |
|
GHSA-g43w-x7fj-gvxf | An issue was discovered in MB CONNECT LINE mymbCONNECT24 and mbCONNECT24 through 2.6.1. There is a blind SQL injection in the knximport component via an advanced attack vector, allowing logged in attackers to discover arbitrary information. | [] | null | null | null | null |
|
CVE-1999-1338 | Delegate proxy 5.9.3 and earlier creates files and directories in the DGROOT with world-writable permissions. | [
"cpe:2.3:a:delegate:delegate:*:*:*:*:*:*:*:*"
] | null | null | null | 5 |
|
CVE-2024-33228 | An issue in the component segwindrvx64.sys of Insyde Software Corp SEG Windows Driver v100.00.07.02 allows attackers to escalate privileges and execute arbitrary code via sending crafted IOCTL requests. | [
"cpe:2.3:a:insyde:seg_windows_driver:*:*:*:*:*:*:*:*"
] | null | 8.4 | null | null |
|
CVE-2023-2649 | Tenda AC23 Service Port 7329 ate command injection | A vulnerability was found in Tenda AC23 16.03.07.45_cn. It has been declared as critical. This vulnerability affects unknown code of the file /bin/ate of the component Service Port 7329. The manipulation of the argument v2 leads to command injection. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used. VDB-228778 is the identifier assigned to this vulnerability. NOTE: The vendor was contacted early about this disclosure but did not respond in any way. | [
"cpe:2.3:o:tenda:ac23_firmware:16.03.07.45_cn:*:*:*:*:*:*:*",
"cpe:2.3:h:tenda:ac23:-:*:*:*:*:*:*:*"
] | null | 7.2 | 7.2 | 8.3 |
GHSA-rp7x-9gh4-8c2q | The Administration page on Connect Box EuroDOCSIS 3.0 Voice Gateway CH7465LG-NCIP-6.12.18.25-2p6-NOSH devices accepts a cleartext password in a POST request on port 80, as demonstrated by the Password field to the xml/setter.xml URI. | [] | null | 7.5 | null | null |
|
GHSA-pf4h-8whx-rxmf | Rockwell Automation PowerFlex 525 AC Drives 5.001 and earlier allow remote attackers to cause a denial of service by crashing the Common Industrial Protocol (CIP) network stack. The vulnerability allows the attacker to crash the CIP in a way that it does not accept new connections, but keeps the current connections active, which can prevent legitimate users from recovering control. | [] | null | null | 9.8 | null |
|
GHSA-gv85-xg33-553c | A vulnerability was discovered in ImageMagick where a specially created SVG file loads itself and causes a segmentation fault. This flaw allows a remote attacker to pass a specially crafted SVG file that leads to a segmentation fault, generating many trash files in "/tmp," resulting in a denial of service. When ImageMagick crashes, it generates a lot of trash files. These trash files can be large if the SVG file contains many render actions. In a denial of service attack, if a remote attacker uploads an SVG file of size t, ImageMagick generates files of size 103*t. If an attacker uploads a 100M SVG, the server will generate about 10G. | [] | null | 5.5 | null | null |
|
CVE-2022-24894 | Symfony storing cookie headers in HttpCache | Symfony is a PHP framework for web and console applications and a set of reusable PHP components. The Symfony HTTP cache system, acts as a reverse proxy: It caches entire responses (including headers) and returns them to the clients. In a recent change in the `AbstractSessionListener`, the response might contain a `Set-Cookie` header. If the Symfony HTTP cache system is enabled, this response might bill stored and return to the next clients. An attacker can use this vulnerability to retrieve the victim's session. This issue has been patched and is available for branch 4.4. | [
"cpe:2.3:a:sensiolabs:symfony:*:*:*:*:*:*:*:*"
] | null | 5.9 | null | null |
CVE-2019-4130 | IBM Cloud Pak System 2.3 and 2.3.0.1 could allow a remote attacker to upload arbitrary files, which could allow the attacker to execute arbitrary code on the vulnerable server. IBM X-Force ID: 158280. | [
"cpe:2.3:a:ibm:cloud_pak_system:2.3:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:cloud_pak_system:2.3.0.1:*:*:*:*:*:*:*"
] | null | null | 9 | null |
|
GHSA-h454-7w34-3fjm | SQL injection vulnerability in index.php in Ovidentia 6.6.5 allows remote attackers to execute arbitrary SQL commands via the field parameter in a search action. NOTE: the provenance of this information is unknown; the details are obtained solely from third party information. | [] | null | null | null | null |
|
CVE-2020-14064 | IceWarp Email Server 12.3.0.1 has Incorrect Access Control for user accounts. | [
"cpe:2.3:a:icewarp:mail_server:12.3.0.1:*:*:*:*:*:*:*"
] | null | 6.5 | null | 4 |
|
GHSA-pj99-jgm5-c727 | The admin panel for Obl.ong before 1.1.2 allows authorization bypass because the email OTP feature accepts arbitrary numerical values. | [] | null | 5.3 | null | null |
|
GHSA-c86w-cch5-3w4m | Atom CMS v2.0 was discovered to contain a reflected cross-site scripting (XSS) vulnerability via the "A" parameter in /widgets/debug.php. | [] | null | 5.4 | null | null |
|
GHSA-whhr-6mwm-777h | In NCH Quorum v2.03 and earlier, XSS exists via User Display Name (stored). | [] | null | null | null | null |
|
RHSA-2023:1892 | Red Hat Security Advisory: java-11-openjdk security update | OpenJDK: improper connection handling during TLS handshake (8294474) OpenJDK: missing string checks for NULL characters (8296622) OpenJDK: incorrect handling of NULL characters in ProcessBuilder (8295304) OpenJDK: Swing HTML parsing issue (8296832) OpenJDK: incorrect enqueue of references in garbage collector (8298191) OpenJDK: certificate validation issue in TLS session negotiation (8298310) OpenJDK: missing check for slash characters in URI-to-path conversion (8298667) | [
"cpe:/a:redhat:rhel_eus:8.6::appstream",
"cpe:/a:redhat:rhel_eus:8.6::crb"
] | null | 3.7 | null | null |
GHSA-m635-gfrg-4wpw | Unspecified vulnerability in the loaders (load_*.php) in Ansilove before 1.03 allows remote attackers to read arbitrary files via unspecified vectors involving "converting files accessible by the webserver". | [] | null | null | null | null |
|
CVE-2023-4907 | Inappropriate implementation in Intents in Google Chrome on Android prior to 117.0.5938.62 allowed a remote attacker to obfuscate security UI via a crafted HTML page. (Chromium security severity: Low) | [
"cpe:2.3:a:google:chrome:*:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:-:*:*:*:*:*:*:*",
"cpe:2.3:o:fedoraproject:fedora:37:*:*:*:*:*:*:*",
"cpe:2.3:o:fedoraproject:fedora:38:*:*:*:*:*:*:*",
"cpe:2.3:o:fedoraproject:fedora:39:*:*:*:*:*:*:*",
"cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"cpe:2.3:o:debian:debian_linux:12.0:*:*:*:*:*:*:*"
] | null | 4.3 | null | null |
|
RHSA-2020:2828 | Red Hat Security Advisory: firefox security update | Mozilla: Memory corruption due to missing sign-extension for ValueTags on ARM64 Mozilla: Information disclosure due to manipulated URL object Mozilla: Use-after-free in nsGlobalWindowInner Mozilla: Use-After-Free when trying to connect to a STUN server Mozilla: Add-On updates did not respect the same certificate trust rules as software updates | [
"cpe:/a:redhat:enterprise_linux:8::appstream"
] | null | 8.8 | 6.1 | null |
CVE-2021-2028 | Vulnerability in the MySQL Server product of Oracle MySQL (component: InnoDB). Supported versions that are affected are 8.0.21 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.1 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H). | [
"cpe:2.3:a:oracle:mysql:*:*:*:*:*:*:*:*",
"cpe:2.3:a:netapp:oncommand_insight:-:*:*:*:*:*:*:*",
"cpe:2.3:a:netapp:oncommand_workflow_automation:-:*:*:*:*:*:*:*",
"cpe:2.3:a:netapp:snapcenter:-:*:*:*:*:*:*:*"
] | null | 4.9 | null | null |
|
GHSA-hr74-rp99-265m | In all Qualcomm products with Android releases from CAF using the Linux kernel, a buffer over-read vulnerability exists in RFA-1x. | [] | null | null | 9.8 | null |
|
GHSA-c2q2-8p87-4x7h | Unspecified vulnerability in the Advanced Queuing component in Oracle Database 10.2.0.4 and 11.1.0.7 allows remote authenticated users to affect confidentiality and integrity, related to SYS.DBMS_AQ_INV. | [] | null | null | null | null |
|
GHSA-5p7c-48hh-g6m7 | NETGEAR RAX30 Improper Certificate Validation Remote Code Execution Vulnerability. This vulnerability allows network-adjacent attackers to compromise the integrity of downloaded information on affected installations of NETGEAR RAX30 routers. Authentication is not required to exploit this vulnerability.The specific flaw exists within the downloading of files via HTTPS. The issue results from the lack of proper validation of the certificate presented by the server. An attacker can leverage this in conjunction with other vulnerabilities to execute arbitrary code in the context of root. Was ZDI-CAN-19589. | [] | null | null | 7.5 | null |
|
GHSA-58gh-w9m3-2whq | Cross-site request forgery (CSRF) vulnerability in the Contextual Related Posts plugin before 1.8.7 for WordPress allows remote attackers to hijack the authentication of administrators for requests that conduct cross-site scripting (XSS) attacks via unspecified vectors. | [] | null | null | null | null |
|
CVE-2014-1403 | Cross-site scripting (XSS) vulnerability in name.html in easyXDM before 2.4.19 allows remote attackers to inject arbitrary web script or HTML via the location.hash value. | [
"cpe:2.3:a:easyxdm:easyxdm:*:*:*:*:*:*:*:*",
"cpe:2.3:a:easyxdm:easyxdm:2.3.2:*:*:*:*:*:*:*",
"cpe:2.3:a:easyxdm:easyxdm:2.3.3:*:*:*:*:*:*:*",
"cpe:2.3:a:easyxdm:easyxdm:2.4.0:*:*:*:*:*:*:*",
"cpe:2.3:a:easyxdm:easyxdm:2.4.1:*:*:*:*:*:*:*",
"cpe:2.3:a:easyxdm:easyxdm:2.4.2:*:*:*:*:*:*:*",
"cpe:2.3:a:easyxdm:easyxdm:2.4.3:*:*:*:*:*:*:*",
"cpe:2.3:a:easyxdm:easyxdm:2.4.4:*:*:*:*:*:*:*",
"cpe:2.3:a:easyxdm:easyxdm:2.4.5:*:*:*:*:*:*:*",
"cpe:2.3:a:easyxdm:easyxdm:2.4.6:*:*:*:*:*:*:*"
] | null | null | null | 4.3 |
|
CVE-2013-5901 | Unspecified vulnerability in the Oracle Identity Manager component in Oracle Fusion Middleware 11.1.2.0 and 11.1.2.1 allows remote attackers to affect confidentiality via unknown vectors related to Identity Console. | [
"cpe:2.3:a:oracle:fusion_middleware:11.1.2.0:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:fusion_middleware:11.1.2.1.0:*:*:*:*:*:*:*"
] | null | null | null | 4.3 |
|
GHSA-3mpj-wgvw-fw9v | SQL Injection vulnerability in HiPresta "Gift Wrapping Pro" (hiadvancedgiftwrapping) module for PrestaShop before version 1.4.1, allows remote attackers to escalate privileges and obtain sensitive information via the HiAdvancedGiftWrappingGiftWrappingModuleFrontController::addGiftWrappingCartValue() method. | [] | null | 9.8 | null | null |
|
GHSA-jh59-pxh9-hgg6 | Multiple cross-site request forgery (CSRF) vulnerabilities in the Thomson/Alcatel SpeedTouch 7G router, as used for the BT Home Hub 6.2.6.B and earlier, allow remote attackers to perform actions as administrators via unspecified POST requests, as demonstrated by enabling an inbound remote-assistance HTTPS session on TCP port 51003. NOTE: an authentication bypass can be leveraged to exploit this in the absence of an existing administrative session. NOTE: SpeedTouch 780 might also be affected by some of these issues. | [] | null | null | null | null |
|
CVE-2022-42891 | A vulnerability has been identified in syngo Dynamics (All versions < VA40G HF01). syngo Dynamics application server hosts a web service using an operation with improper write access control that could allow to write data in any folder accessible to the account assigned to the website’s application pool. | [
"cpe:2.3:a:siemens:syngo_dynamics_cardiovascular_imaging_and_information_system:*:*:*:*:*:*:*:*"
] | null | 7.5 | null | null |
|
GHSA-w437-cqhg-f7j8 | Apache CouchDB before 1.0.4, 1.1.x before 1.1.2, and 1.2.x before 1.2.1 allows remote attackers to execute arbitrary code via a JSONP callback, related to Adobe Flash. | [] | null | null | null | null |
|
GHSA-gccx-g2pg-5r7x | Cisco UCS Invicta C3124SA Appliance 4.3.1 through 5.0.1, UCS Invicta Scaling System and Appliance, and Whiptail Racerunner improperly store a default SSH private key, which allows remote attackers to obtain root access via unspecified vectors, aka Bug ID CSCun71294. | [] | null | null | 9.8 | null |
|
CVE-2022-41408 | Online Pet Shop We App v1.0 was discovered to contain a SQL injection vulnerability via the id parameter at /admin/?page=orders/view_order. | [
"cpe:2.3:a:online_pet_shop_we_app_project:online_pet_shop_we_app:1.0:*:*:*:*:*:*:*"
] | null | 9.8 | null | null |
|
CVE-2017-1342 | IBM Insights Foundation for Energy 2.0 could reveal sensitive information in error messages to authenticated users that could e used to conduct further attacks. IBM X-Force ID: 126457. | [
"cpe:2.3:a:ibm:insights_foundation_for_energy:2.0:*:*:*:*:*:*:*"
] | null | null | 4.3 | 4 |
|
GHSA-3p58-8w88-7f88 | Multiple directory traversal vulnerabilities in the mod_site_misc module in ProFTPD before 1.3.3c allow remote authenticated users to create directories, delete directories, create symlinks, and modify file timestamps via directory traversal sequences in a (1) SITE MKDIR, (2) SITE RMDIR, (3) SITE SYMLINK, or (4) SITE UTIME command. | [] | null | null | null | null |
|
CVE-2014-0282 | Microsoft Internet Explorer 6 through 11 allows remote attackers to execute arbitrary code or cause a denial of service (memory corruption) via a crafted web site, aka "Internet Explorer Memory Corruption Vulnerability," a different vulnerability than CVE-2014-1775, CVE-2014-1779, CVE-2014-1799, CVE-2014-1803, and CVE-2014-2757. | [
"cpe:2.3:a:microsoft:internet_explorer:6:*:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:internet_explorer:7:*:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:internet_explorer:8:*:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:internet_explorer:9:*:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:internet_explorer:10:*:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:internet_explorer:11:-:*:*:*:*:*:*"
] | null | null | null | 9.3 |
|
GHSA-mh9f-g72r-hf94 | Buffer overflow in IBM Platform Symphony 5.2, 6.1, and 6.1.1 allows remote attackers to cause a denial of service (process crash or hang) via a malformed SOAP request with a large amount of request data. | [] | null | null | null | null |
|
CVE-2022-46583 | TRENDnet TEW755AP 1.13B01 was discovered to contain a stack overflow via the reboot_type parameter in the wizard_ipv6 (sub_41C380) function. | [
"cpe:2.3:o:trendnet:tew-755ap_firmware:1.13b01:*:*:*:*:*:*:*",
"cpe:2.3:h:trendnet:tew-755ap:-:*:*:*:*:*:*:*"
] | null | 9.8 | null | null |
|
CVE-2010-3854 | Multiple cross-site scripting (XSS) vulnerabilities in the web administration interface (aka Futon) in Apache CouchDB 0.8.0 through 1.0.1 allow remote attackers to inject arbitrary web script or HTML via unspecified vectors. | [
"cpe:2.3:a:apache:couchdb:0.8.0:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:couchdb:0.8.1:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:couchdb:0.9.0:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:couchdb:0.9.1:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:couchdb:0.9.2:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:couchdb:0.10.0:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:couchdb:0.10.1:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:couchdb:0.10.2:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:couchdb:0.11.0:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:couchdb:0.11.1:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:couchdb:0.11.2:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:couchdb:1.0.0:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:couchdb:1.0.1:*:*:*:*:*:*:*"
] | null | null | null | 4.3 |
|
GHSA-5r72-jhpg-7v5v | Windows Kernel Information Disclosure Vulnerability. This CVE ID is unique from CVE-2022-30197. | [] | null | 5.5 | null | null |
|
GHSA-fhr5-r945-frm5 | Sourcecodester Online Thesis Archiving System 1.0 is vulnerable to SQL Injection. An attacker can bypass admin authentication and gain access to admin panel using SQL Injection | [] | null | null | null | null |
|
GHSA-626c-c4r3-vmjg | Foxit PDF Reader AcroForm Use-After-Free Remote Code Execution Vulnerability. This vulnerability allows remote attackers to execute arbitrary code on affected installations of Foxit PDF Reader. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file.The specific flaw exists within the handling of AcroForms. The issue results from the lack of validating the existence of an object prior to performing operations on the object. An attacker can leverage this vulnerability to execute code in the context of the current process. Was ZDI-CAN-23928. | [] | null | null | 7.8 | null |
|
CVE-2007-3333 | Stack-based buffer overflow in capture in IBM AIX 5.3 SP6 and 5.2.0 allows remote attackers to execute arbitrary code via a large number of terminal control sequences. | [
"cpe:2.3:o:ibm:aix:5.2.0:*:*:*:*:*:*:*",
"cpe:2.3:o:ibm:aix:5.3:sp6:*:*:*:*:*:*"
] | null | null | null | 6.9 |
|
GHSA-f8mm-mpjv-c2qm | Integer overflow in the simulator in Swift in Apple Xcode before 6.3 allows context-dependent attackers to cause a denial of service or possibly have unspecified other impact by triggering an incorrect result of a type conversion. | [] | null | null | null | null |
|
CVE-2022-24116 | Certain General Electric Renewable Energy products have inadequate encryption strength. This affects iNET and iNET II before 8.3.0. | [
"cpe:2.3:o:ge:inet_900_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:ge:inet_900:-:*:*:*:*:*:*:*",
"cpe:2.3:o:ge:inet_ii_900_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:ge:inet_ii_900:-:*:*:*:*:*:*:*",
"cpe:2.3:o:ge:sd1_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:ge:sd1:-:*:*:*:*:*:*:*",
"cpe:2.3:o:ge:sd2_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:ge:sd2:-:*:*:*:*:*:*:*",
"cpe:2.3:o:ge:sd4_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:ge:sd4:-:*:*:*:*:*:*:*",
"cpe:2.3:o:ge:sd9_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:ge:sd9:-:*:*:*:*:*:*:*",
"cpe:2.3:o:ge:td220max_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:ge:td220max:-:*:*:*:*:*:*:*",
"cpe:2.3:o:ge:td220x_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:ge:td220x:-:*:*:*:*:*:*:*"
] | null | 9.8 | null | null |
|
RHSA-2021:3281 | Red Hat Security Advisory: rh-nodejs12-nodejs and rh-nodejs12-nodejs-nodemon security update | nodejs-ini: Prototype pollution via malicious INI file nodejs-glob-parent: Regular expression denial of service c-ares: Missing input validation of host names may lead to domain hijacking nodejs: Use-after-free on close http2 on stream canceling nodejs: Improper handling of untypical characters in domain names nodejs: Incomplete validation of tls rejectUnauthorized parameter nodejs: Use-after-free on close http2 on stream canceling nodejs-path-parse: ReDoS via splitDeviceRe, splitTailRe and splitPathRe nodejs-tar: Insufficient symlink protection allowing arbitrary file creation and overwrite nodejs-tar: Insufficient absolute path sanitization allowing arbitrary file creation and overwrite | [
"cpe:/a:redhat:rhel_software_collections:3::el7"
] | null | 8.1 | null | null |
GHSA-8jmh-wwh6-r8gj | An Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') vulnerability in the Schweitzer Engineering Laboratories Real-Time Automation Controller (SEL RTAC) Web Interface could allow a remote authenticated attacker to inject and execute arbitrary script code.See SEL Service Bulletin dated 2022-11-15 for more details. | [] | null | 4.3 | null | null |
|
CVE-2024-46781 | nilfs2: fix missing cleanup on rollforward recovery error | In the Linux kernel, the following vulnerability has been resolved:
nilfs2: fix missing cleanup on rollforward recovery error
In an error injection test of a routine for mount-time recovery, KASAN
found a use-after-free bug.
It turned out that if data recovery was performed using partial logs
created by dsync writes, but an error occurred before starting the log
writer to create a recovered checkpoint, the inodes whose data had been
recovered were left in the ns_dirty_files list of the nilfs object and
were not freed.
Fix this issue by cleaning up inodes that have read the recovery data if
the recovery routine fails midway before the log writer starts. | [
"cpe:2.3:o:linux:linux_kernel:*:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.11:rc1:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.11:rc2:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.11:rc3:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.11:rc4:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.11:rc5:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.11:rc6:*:*:*:*:*:*"
] | null | 5.5 | null | null |
CVE-2008-5241 | Integer underflow in demux_qt.c in xine-lib 1.1.12, and other 1.1.15 and earlier versions, allows remote attackers to cause a denial of service (crash) via a crafted media file that results in a small value of moov_atom_size in a compressed MOV (aka CMOV_ATOM). | [
"cpe:2.3:a:xine:xine-lib:*:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:0.9.13:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1:rc0a:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1:rc1:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1:rc2:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1:rc3:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1:rc3a:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1:rc3b:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1:rc3c:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1:rc4:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1:rc4a:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1:rc5:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1:rc6a:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1:rc7:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1:rc8:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1.0:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1.0.1:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1.0.2:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1.0.3a:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1.1.0:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1.1.1:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1.1.2:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1.1.3:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1.1.4:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1.1.5:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1.1.6:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1.1.7:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1.1.8:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1.1.9:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1.1.9.1:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1.1.10:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1.1.10.1:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1.1.11:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1.1.11.1:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1.1.12:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1.1.13:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1.1.14:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1_beta1:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1_beta2:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1_beta3:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1_beta4:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1_beta5:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1_beta6:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1_beta7:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1_beta8:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1_beta9:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1_beta10:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1_beta11:*:*:*:*:*:*:*",
"cpe:2.3:a:xine:xine-lib:1_beta12:*:*:*:*:*:*:*"
] | null | null | null | 4.3 |
|
GHSA-8345-rfq2-7h8q | An authentication bypass vulnerability in Kentico Xperience allows authentication bypass via the Staging Sync Server component password handling for the server defined None type. Authentication bypass allows an attacker to control administrative objects.This issue affects Xperience through 13.0.178. | [] | null | 9.8 | null | null |
|
CVE-2025-1818 | zj1983 zz ZfileAction.upload unrestricted upload | A vulnerability, which was classified as critical, has been found in zj1983 zz up to 2024-8. This issue affects some unknown processing of the file src/main/java/com/futvan/z/system/zfile/ZfileAction.upload. The manipulation of the argument file leads to unrestricted upload. The attack may be initiated remotely. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way. | [] | 5.3 | 6.3 | 6.3 | 6.5 |
GHSA-h2c9-6vfm-cc58 | Adobe ColdFusion versions Update 14 (and earlier) and Update 4 (and earlier) are affected by a Heap-based Buffer Overflow vulnerability that could result in arbitrary code execution in the context of the current user. Exploitation of this issue does not require user interaction, the vulnerability is triggered when a crafted network packet is sent to the server. | [] | null | 9.8 | null | null |
|
CVE-2004-1055 | Multiple cross-site scripting (XSS) vulnerabilities in phpMyAdmin 2.6.0-pl2 and earlier allow remote attackers to inject arbitrary web script or HTML via (1) the PmaAbsoluteUri parameter, (2) the zero_rows parameter in read_dump.php, (3) the confirm form, or (4) an error message generated by the internal phpMyAdmin parser. | [
"cpe:2.3:a:phpmyadmin:phpmyadmin:2.5.0:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:2.5.1:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:2.5.2:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:2.5.4:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:2.5.5:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:2.5.5_pl1:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:2.5.5_rc1:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:2.5.5_rc2:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:2.5.6_rc1:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:2.5.7:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:2.5.7_pl1:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:2.6.0_pl1:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:2.6.0_pl2:*:*:*:*:*:*:*",
"cpe:2.3:o:gentoo:linux:1.4:*:*:*:*:*:*:*",
"cpe:2.3:o:gentoo:linux:1.4:rc1:*:*:*:*:*:*",
"cpe:2.3:o:gentoo:linux:1.4:rc2:*:*:*:*:*:*",
"cpe:2.3:o:gentoo:linux:1.4:rc3:*:*:*:*:*:*"
] | null | null | null | 6.8 |
|
GHSA-q562-q3f3-pjg8 | Cross-site scripting (XSS) vulnerability in ow-shared.pl in OpenWebMail (OWM) 2.51 and earlier allows remote attackers to inject arbitrary web script or HTML via the sessionid parameter in (1) openwebmail-send.pl, (2) openwebmail-advsearch.pl, (3) openwebmail-folder.pl, (4) openwebmail-prefs.pl, (5) openwebmail-abook.pl, (6) openwebmail-read.pl, (7) openwebmail-cal.pl, and (8) openwebmail-webdisk.pl. NOTE: the openwebmail-main.pl vector is already covered by CVE-2005-2863. | [] | null | null | null | null |
|
GHSA-5w44-c9q8-9w9v | Userspace-controlled non null terminated parameter for IPA WAN ioctl in all Qualcomm products with Android releases from CAF using the Linux kernel can lead to exposure of kernel memory. | [] | null | null | 5.5 | null |
|
CVE-2016-0331 | Cross-site scripting (XSS) vulnerability in IBM Rational Team Concert 6.0.1 and 6.0.2 before 6.0.2 iFix2 and Rational Collaborative Lifecycle Management 6.0.1 and 6.0.2 before 6.0.2 iFix2 allows remote authenticated users to inject arbitrary web script or HTML via a crafted URL. | [
"cpe:2.3:a:ibm:rational_collaborative_lifecycle_management:6.0.1:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:rational_collaborative_lifecycle_management:6.0.2:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:rational_team_concert:6.0.1:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:rational_team_concert:6.0.2:*:*:*:*:*:*:*"
] | null | null | 5.4 | 3.5 |
|
GHSA-vrg4-hqcw-hjvg | URL Redirection to Untrusted Site ('Open Redirect') vulnerability in Heateor Support Sassy Social Share allows Phishing. This issue affects Sassy Social Share: from n/a through 3.3.73. | [] | null | 4.7 | null | null |
|
PYSEC-2025-12 | null | CodeChecker is an analyzer tooling, defect database and viewer extension for the Clang Static Analyzer and Clang Tidy.
Cross-site request forgery allows an unauthenticated attacker to hijack the authentication of a logged in user, and use the web API with the same permissions, including but not limited to adding, removing or editing products. The attacker needs to know the ID of the available products to modify or delete them. The attacker cannot directly exfiltrate data (view) from CodeChecker, due to being limited to form-based CSRF.
This issue affects CodeChecker: through 6.24.4. | [] | null | null | null | null |
GHSA-qc22-6662-58rj | A technical user has hardcoded credentials in Wallstreet Suite TRM 7.4.83 (64-bit edition) with higher privilege than the average authenticated user. | [] | null | null | null | null |
Subsets and Splits
No saved queries yet
Save your SQL queries to embed, download, and access them later. Queries will appear here once saved.